Hexa Payload Decoder Tool: A Tool To Automatically Extract and Decode Hex Data in C&C Servers
A Tool To Automatically Extract and Decode Hex Data in C&C Servers
This tool is able to process a pcap file and return any decoded characters translated to English. The tool automates and speeds up the manual process previously done by the human analyst.
The tool receives a pcap extension network analysis file, filters all TCP traffic, obtains the data encoded in the hexadecimal system, decodes it including all characters (both the most used and the least known), detects the language and translates them into English. This is possible because the tool, written in Bash scripting language, uses three key tools: Tshark [1], a tool for filtering and analyzing network floppies to filter TCP packets; CyberChef [2], an advanced decoding tool written in Javascript script language; and GoogleTrans [3], a Python scripting language library that detects and translates any language.
The Hexa Payload Decoder tool is able to process a pcap file and output any identified encoded strings, decoded and translated to English.
Use case example
To perform network malware analysis the research team infects Raspberry Pi (RPI) devices in a controlled network connected to the internet. During the analysis of CTU-IoT-Malware-Capture-52-1, one of the network traffic captures of the infected RPI devices, we found some suspicious behaviours:
The infected device maintained long-term communications in time and with a large amount of data exchange with a server with IP 185.244.25.108 to port 4441
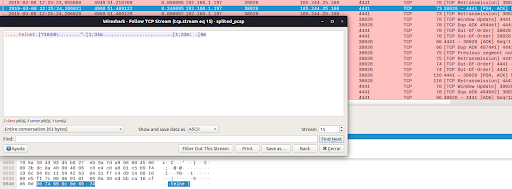
When analyzing the TCP traffic to destination port 4441 we found data in hexadecimal format which were mostly interpreted by the well-known Wireshark network traffic analysis tool:
One of the payloads in the hexadecimal system found with a length of 7 bytes was "0674656c6e 6574" and was decoded by Wireshark as the string in ASCII ".telnet".
Another more interesting data payload in hexadecimal system with length of 44 bytes "1b5b313b33346dd0bfd0bed0bbd18cd0b7d0bed0b2d0b0d182d0b5d0bbd18c1b5b313b33336d3a201b5b306d" was decoded by Wireshark as the ASCII string: "[1;34m.........................[1;33m: .[0m" . This decoding that gives us very little information.
When analyzing the long suspicious payload with various tools that convert hexadecimal to ASCII, we did not obtain any coherent response.
Using the multi purpose decoding tool CyberChef gave us the following result: ". [1; 34mпользователь. [1; 33m: . [0m" which translated with the GoogleTrans Python library from Russian into English turns out to be the word "user" between ANSI codes used to give color to the characters in terminal systems.
Figure 2: Suspicious data finding at Mirai port 4441 in Wireshark and its TCP Stream. The decoded hexadecimal payload cant be read with Wireshark.
Figure 3: Running the Hexadecimal Decoding and Translating tool with the suspicious port 4441 TCP Stream pcap file.
Figure 4: Checking the results of the analysis done. The word user in Russian can be seen after the decoding and translating process.
Download
Link to the tool: https://github.com/stratosphereips/Hexa_Payload_Decoder/blob/master/README.md