An entry from '/etc/passwd' explained
The passwd file contains information about the users, ,their login name, user and group IDs, home directory and other information. [[Read more]]
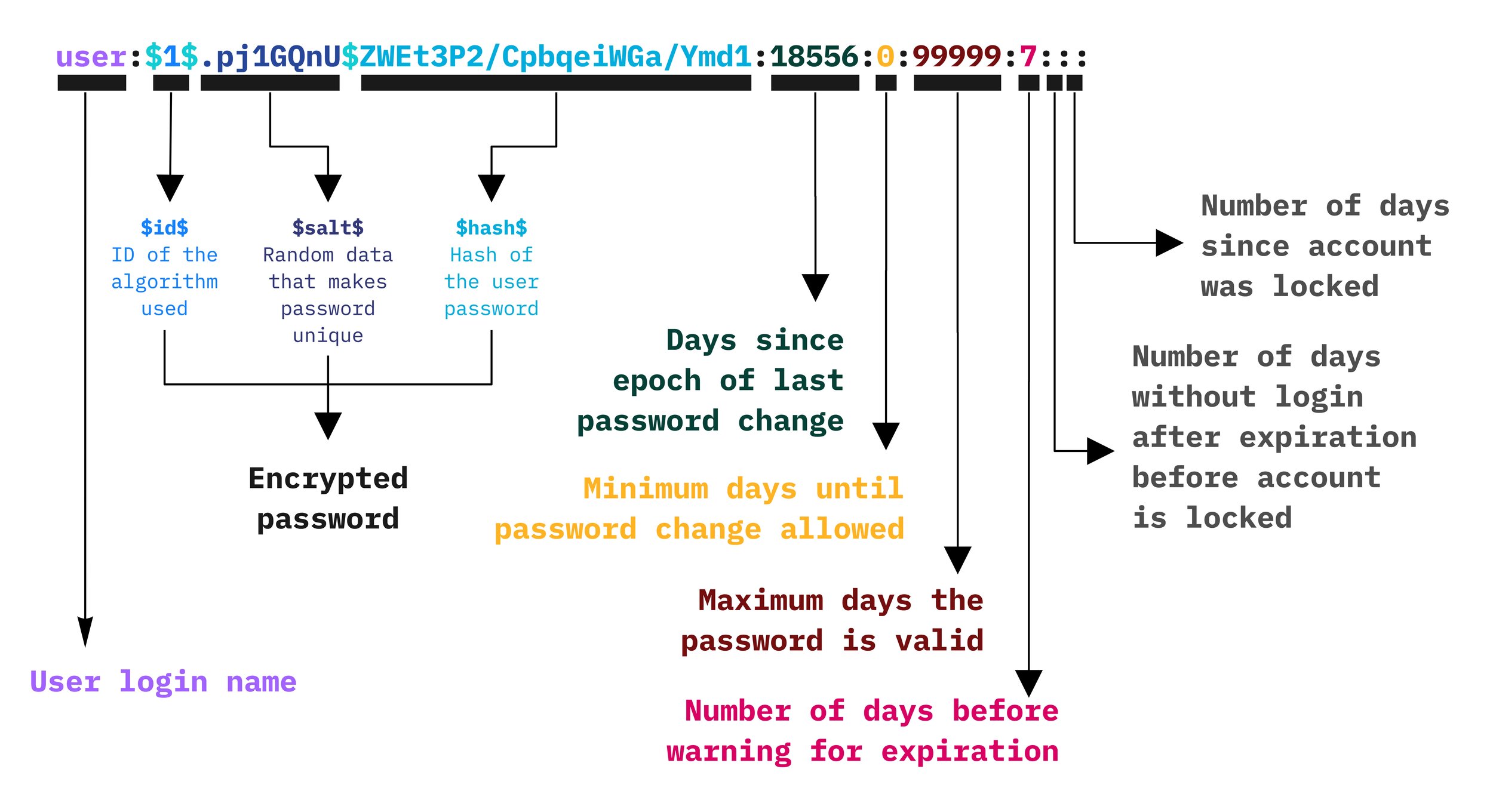
An entry from '/etc/shadow' explained
The shadow file contains the actual user encrypted password along with other information. [[Read more]]