On Wednesday, October 2, at the 29th Virus Bulletin International Conference (VB2019) in London, our researchers Veronica Valeros, Maria Rigaki, Kamila Babayeva and Sebastian Garcia will present the results of more than 3 years of studying and tracking the Machete APT in their talk “A Study of Machete Cyber Espionage Operations in Latin America”.
Hexa Payload Decoder Tool: A Tool To Automatically Extract and Decode Hex Data in C&C Servers
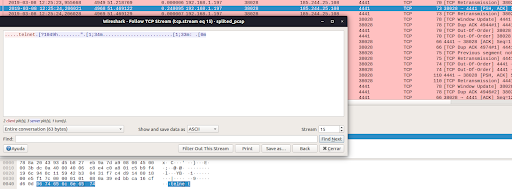
In this blog post we introduce the “Hexa Payload Decoder Tool”, a tool that is able to process a pcap file and return any decoded characters translated to English. This tool was developed to assist the network security analyst when working and interpreting data sent and received by command and control servers used by malware.
Upcoming Talk: Geost botnet. The discovery story of a new Android banking trojan from an OpSec error
On October 2019, Virus Bulletin conference will be held in London. Our researchers Sebastián García, María José Erquiaga and Anna Shirokova will be presenting their research on the novel Geost botnet.
Upcoming Talk: A Study of Machete Cyber Espionage Operations in Latin America
On Wednesday, October 2, at the 29th Virus Bulletin International Conference (VB2019) in London, our researchers Veronica Valeros, Maria Rigaki, Kamila Babayeva and Sebastian Garcia will present the results of more than 3 years of studying and tracking the Machete APT in their talk “A Study of Machete Cyber Espionage Operations in Latin America”.
DEFCON 2019. Beyond Sandboxes. How to Execute IoT Malware and Analyze its Evolution
Project Ludus - Smart Honeypot Manager for Collaborative Defense
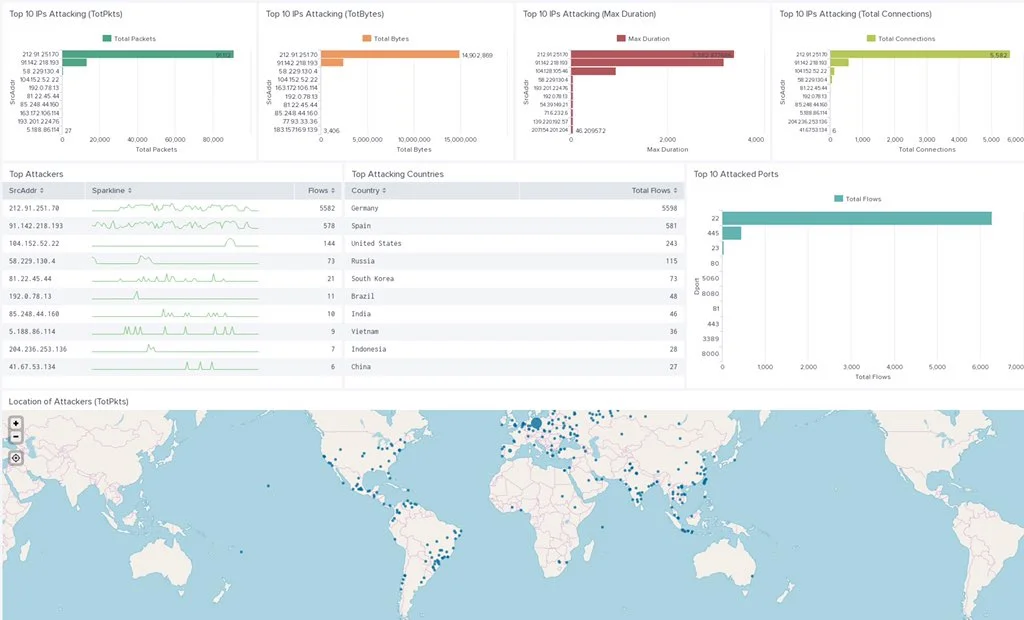
In this blogpost we introduce our tool which uses honeypots as a defense mechanism based on the game theoretical model of behavior of the attackers. Ludus fully automates honeypot deployment and management and visualize results in the level of individual routers. [Read more]
IoT Honeypot Traffic Analysis Series. Analysis of Edimax IC-7113W, part 4
In this IoT Honeypot Analysis Series, we focus on the traffic analysis of the Edimax IC-7113W camera. In this episode, we will continue with the analysis of the encrypted packets mentioned in the previous episode. Our goals for this blog post are:
to obtain the AES key from the Edimax server
to understand what happens with the communication after we obtain the AES key
to get a plaintext of the encrypted payload sent from the camera to the server
Summary of the Amparo-CERTUNLP Workshop in Neuquén, Argentina
On May 27-30 I participated as member of the CERTUNLP in a conference organized by the Government of Neuquén province in Argentina. Together with LACNIC in the frame of the Amparo Project we participated giving a workshop to other incident responders and members of CSIRTs. The event was very successful. The audience gathered individuals responsible for the security area of many Argentine provinces as well as National Universities, representatives of local ISPs, banks and other public and private organizations. By Paula Venosa.
First Workshop on Attackers and Cyber-Crime Operations (WACCO) 2019
On June 20th will take place in Stockholm the First Workshop on Attackers and Cyber-Crime Operations (WACCO) as part of the IEEE European Symposium on Security and Privacy (EuroSP). WACCO is a great initiative that provides the opportunity for research, discussions, and sharing on cyber-criminal activities.
Getting Started With Splunk: Basic Searching & Data Viz
IoT Honeypot Traffic Analysis Series. Analysis of Edimax IC-7113W, part 3
OWASP CZ 2019: Conference Wrap-Up
Aposemat IoT Malware Analysis, an X-Bash infection
IoT Malware Analysis Series. An IoT malware dropper with custom C&C channel exploiting HNAP
Analysis of an IRC based Botnet
This blogpost aims to give an insight of an IRCBased botnet describing the network behavior and showing the analysis of the C&C. By analyzing this botnet network traffic it was possible to identify the botmasters using an IRC channel and observe not only the conversation between them but also the orders they give to the bot.
IoT Honeypot Traffic Analysis Series. Continuation Analysis of Honeypot Camera Traffic Edimax IC-7113W
What do we know about Quasar RAT? A review.
IoT Honeypot Traffic Analysis Series. Analysis of Edimax IC-7113W
BlackHoodie Bootcamp #4 Wrap Up - Berlin 2018
his year we were lucky to be able to attend the 4th edition of the BlackHoodie Bootcamp in Berlin. BlackHoodie is a women-only reverse engineering [intensive] bootcamp, meant to introduce attendees to reverse engineering and other highly technical areas of information security in an intensive weekend. Born in 2015 with only 15 attendees, BlackHoodie has grown now to over 90 participants from all over the world.
Live Class Machine Learning for Network Security
This is the training class “Machine Learning para Seguridad en Redes y Detección de Malware” for the CACIC 2018 Conference.
The live video of the class will be added here soon.